First. the only string reference pointed to this section :
What is this Blog About ?
It is about a minor project that i recently completed. That is writing a virtual machine to slow down the process of reverse engineering. This is not a tutorial to do the same however I have included the presentation that i used during the final presentation, the PDFs for System Design and Sample Runs and one step by step sample run. Continue Reading
A note to the technical reader : This is basically a custom loader I wrote so that i could edit the return address of functions on the stack.
Hi, non technical reader. Continue Reading
Hey,
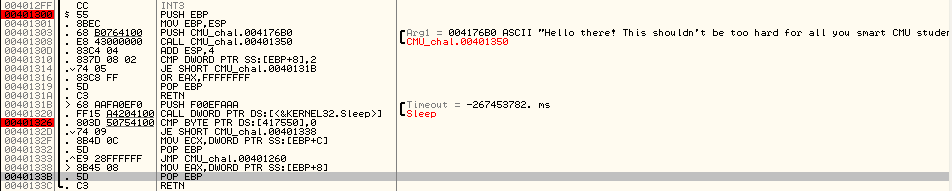
So moving on to a relatively advanced API based debugger detection or anti-debugging techniques, i am going to today discuss the implmentation of ZwSetInformationThread routine. Now this is an undocumented win32 API and we need to get a pointer to the function inside a library and then make a call to the function. The very first implementation is as follows (by the way I code on Code:Blocks 12.11): Continue Reading
Hi,
I am currently working on anti-debugging techniques which will also be my project for this year in college.Though i know for a fact most basic anti-debug techniques are API based techniques, but i am still doing this post because firstly i did not find any working code and whatever non-working code was present was also implemented locally… By the way I am really impressed by the work compiled by Tyler Shields in 2009 and he has put up some of the best resources out there!
This post is basically about one of those standard API’s > CheckRemoteDebuggerPresent function. Continue Reading
The very first Humla session at Null Delhi Chapter meet. Awkay, I am going to try and make this not sound like Chinese to people who have, no idea about what this is.
So “null” is an open community. Created and run by Aseem Jahakar sir, nation wide(india). This community is for hackers, for anybody and everybody who relates or wishes to relate him/herself with security. Atleast that’s what I have experienced till now! :) Continue Reading
I have had a severe sprain in my neck for around 3 days now and was looking for “something different” to do after i get well. Also I had been writing an article on the cross-site scripting framework for the college’s annual magazine. (you will know where am I going with this soon). So as I was thinking it came to me that ” watching theatre” could be the “something different”. Continue Reading
What is a .onion website?
The .onion website would be an http service hosted on your localhost and accessed by the TOR browser only.
What is the TOR browser?
It is a browser that looks like mozilla firefox and can give you a completely anonymous browsing. Continue Reading
Hi there,
So today ie 18th august 2012. I attended my first null meet. I actually liked the concept there..wait let me start from the beginning. So i received the email regarding the Delhi meet… and after a little hesitation asked Mr. Aseem Jahakar if the meet would allow some on the spot presentations. He said that its planned before hand so, I need to tell him in advance if I wish to make a presentation. So, I told him that I am working on the project …the PBX vulnerabilities …but haven’t completed it yet. Continue Reading
Hi, so we have this subject called DBMS (database management system) which is taken up by Miss. Nishtha Jatana. Nishtha maam follows a different routine for her classes…a rather constructive one. She converts her initial 2 – 3 tutorial classes into presentations that are delivered by the students. If you don’t know what a tutorial class is.. it is basically a kind of an extra class where students can ask doubts or there can be revision of topics or some numerical problems related to the topics can be done. Now the presentations are conducted on a voluntary basis. There is no compulsion, so i decided Continue Reading